Our Offerings
If you want to learn more, please contact us and we will reach out to you.
Top 10 Cyber Security Project ideas
1. CAESAR CIPHER – ENCRYPTION/DECRYPTION
When you start your journey into Cryptography, one of the basic encryption techniques you will learn is the Caesar Cipher.
The cipher is almost a thousand years old and was used in the time of Roman dictator Julius Caesar who used this cipher to provide cryptic orders to his army.
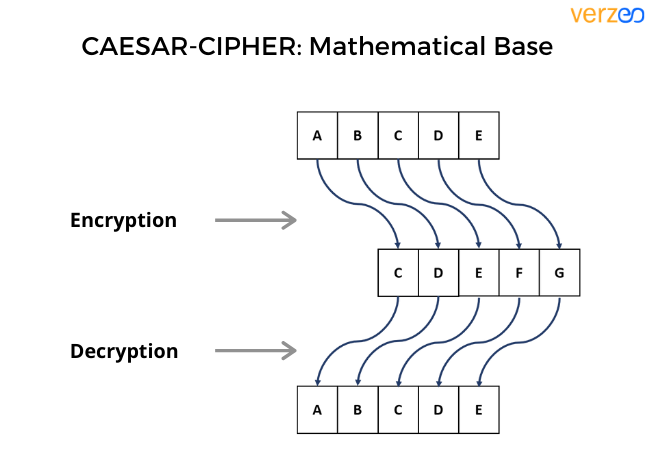
This simple mini project on Cybersecurity offers you the opportunity to work on and understand encryption and decryption using Caesar Cipher. The project follows the simple logic of a numeric cipher value that is used to shift the place values of respective alphabets of a certain text.
For example: For a text, say VERZEO if we apply a cipher value (also known as a key) of 3, then the alphabets are shifted to the right of it by that many times.
So VERZEO becomes, YHUCHR which is also known as the ciphertext. The same trick is applied to retrieve the normal text.
You can create the Cipher using a Program across any programming language that can work on the encryption and decryption of the given text.
2. KEYSTROKE LOGGER
A Keystroke logger is used to collect and log the entry data of people who have used the system through monitoring from the mainframe (which is another computer). This Keystroke logger can maintain records of system activity.
It is also used for hacking user information that is considered important and tangible. It is used by shrouded hackers who work in the dark to track and obtain all your information while you browse a site like say a banking app or website and retrieve all data illegally.
This cybersecurity project involves coding using any programming language to track the activity in a particular system during usage of the system to log all keystrokes that happen.
3. HASH FUNCTION(S)
A hash function is similar to a cipher function and converts a text to be encrypted into a random set of characters that can’t be retrieved illegally by third parties.
There are multiple layers of encryption that are involved in creating a Hash Function and that makes it tougher for hackers.
This is a typical Python Cybersecurity project and involves creating Hash Functions out of a number of passwords created by you (or your fellow programmer) using exception handles and loops concepts.
4. PACKET SNIFFING
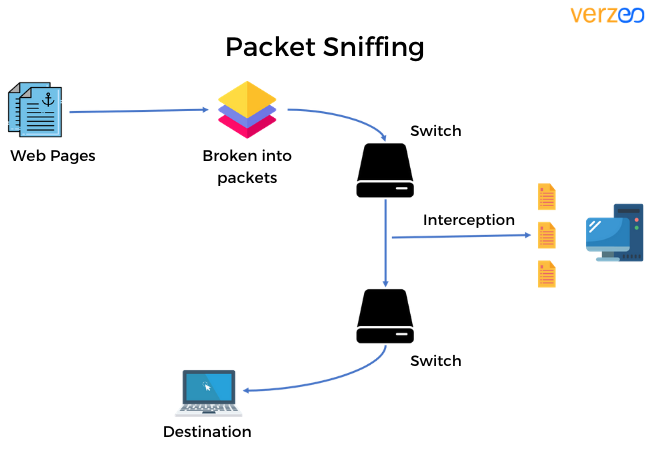
This is another method that is used prevalently by cybersecurity experts within the industry to have a track of the transmission of information through their network.
A Packet typically contains the information (or) data that is to be transmitted across two locations within the network from the sender to the intended receiver.
Using this technique, we can track and monitor the progress of the packets that transmit the data from the source to the destination.
For this cybersecurity project, you can either work through Python programs to track the information contained within the packet or with their intended source and destination.
You can also create a system that can track any illegal retrieval of sensitive information or ensure that the infrastructure around this packet transmission is safe from external intrusions.
5. SQL INJECTION VULNERABILITY ASSESSMENT
An SQL Injection is an attack that is focused on infiltrating the proprietary data of an individual, group, or organization and can manipulate the same.
It is considered one of the most dangerous attacks on data in the cybersecurity industry and there are plenty of practices performed on part of the companies to safeguard their databases from this attack.
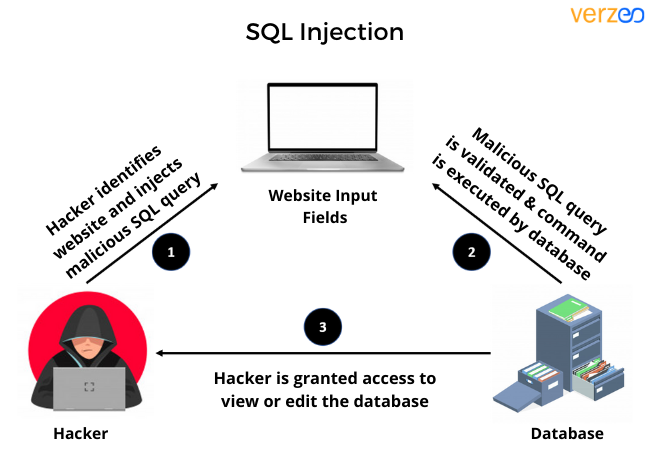
For this ethical hacking project, you will be working on the vulnerable areas of any database, be it of a website, a school marks system or any entity that houses a data recording system. You can also work on proprietary websites but it would require working with prior permission.
You can also work on ideas to create a foolproof system that would prevent these attacks in the future.
6. ONLINE FUND TRANSFERS USING DES ENCRYPTION
Financial Services have been never easy with the infiltration of Internet banking services that are offered by customers to finish all their financial transactions at the click of a few buttons.
These places though are to be safeguarded heavily as they involve people on the dark end that are ready to pounce on the opportunity to retrieve data of the innocent and unaware customers and siphon off their money. The responsibility is on the bank to create safe firewalls around these transactions.
For this practice, a very powerful cryptographic algorithm can be used called the DES Algorithm. The DES Algorithm deals in 64-bit blocks and works through multiple steps and layers that involve turning the content into cryptic content, decrypt, and then re-encrypt the information multiple times. This ensures that there is uncertainty around the state of the content.
Using this technique and the possible hash function that you can create, you can provide unique OTPs for the user to authorize their transactions.
7. IMAGE ENCRYPTION
This is one of the most interesting network security projects regarding Image Encryption and will entail sending images and visual data on a remote server to the intended recipient.
You can work on creating a system or software where you can connect your users remotely and through security measures such as login etc.
Once they are registered, you can set up your transfer system and protect it using powerful algorithms like DES, AES, and/or RSA Algorithm. The choice of algorithm is left to you, and you can link up multiple sources for transfer such as sending through remote servers and networks and encrypting them using keys.
Hence, even if an attacker gets access to these images, they would be encrypted and the attacker must have the relevant keys to decrypt them which he/she won’t. You can experiment it by working on a website or software or any application of your choice which improves your web development skills as well.
8. CREDIT CARD FRAUD DETECTION
The project involving Credit Card Fraud Detection is one of the most prescribed cybersecurity projects for beginners and involves some complex coding but pretty simple understanding.
The idea is pretty simple, Credit cards involve loads of money that are always in the eye of intruders who want to siphon information and the funds involved. Our project will work on ensuring that this information is never compromised.
This project will involve working on a system that analyzes users’ transactions and their behaviors. Based on this research (that your system is capable of doing), your system will ascertain parameters for any unusual behavior in the system like false passwords or illegal entry into the system.
Based on this, the system can introduce countermeasures that will act on the intruder and block him out. The information regarding login will be passed on to the real user and will make them aware of the same. This project involves analyzing the user’s behavior and location.
9. INTERNET BORDER PATROL
This project will see you working on a system that declutters undesirable traffic on a website (example). The system will look for unresponsive packets in the network and remove them. These packets can clog the network at times and make it difficult for people to browse later.
This approach called “Internet Border Patrol” helps to control any type of network congestions. The project would involve the creation of the system using scripted language and base Python programming that provides conditions to check for unresponsive packets in the network.
Unresponsive packets can be utilized by malicious users who may fill in viruses and worms that can attack, compromise, and/or destroy the entire system. Hence, this project/technique helps in declogging the network and also ensuring that there are no stray packets that may be misused.
10. CAPTCHA IMAGES
A simple yet interesting Cybersecurity project to round out our list. Remember those dialog boxes that ask you to choose the right squares containing certain objects to prove that “you are not a robot” while you log into a website?
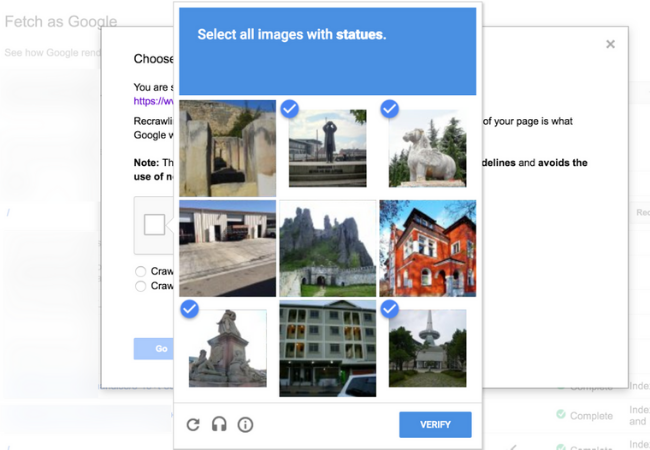
Now that you know it, you can also work on this as a project as well. It is used to provide security and integrity to availing any data or quantifiable asset. How your project can differ is, you can use chosen images by the registered user for the retrieval of this information along with certain security questions and other features.
For example: When a user wants to log in to your system, say for a bank, they can choose the image that they want to secure their account with. Another time, they can access using the same with a set of security questions to be answered.
Of course, the backend of this is also to be created and can be created using Python and PHP programming. For image recognition, you might be required to have some knowledge of Deep Learning as well.
How would these Cyber Security project ideas help you?
These Cybersecurity projects will instill qualities such as programming skills, analytical ability, and temperament while handling complex situations such as building security systems.
This field requires mental ability to withstand attacks as well as the quick-feet to know which algorithm or technique to use while creating foolproof systems or safeguarding the information which might be under attack.
Project experience is now considered invaluable as it gives evidence of your hands-on capability in the domain and is considered in great reference within the technological industry. Cybersecurity is no exception to this.
Concluding Cyber Security project ideas
As per reports from popular firms like AT&T and Gartner Analytics:
- Organizations are spending an average of 5.6% of their IT budget on Cybersecurity
- In 2019, the United States Government’s annual budget included an expenditure of US$ 15 billion on improving its security systems alone (0.3% of total budget)
- Fintech and Financial Services companies spend the most on Cybersecurity practices and infrastructure with a reported 10% average expenditure of their budgets.
The future of Cybersecurity is bright with the industry expected to be worth close to US$250 billion by 2023 (10.2% CAGR).
More than 3.5 million jobs are expected to be open within cybersecurity by 2021 (a 350% increase from last decade) making it the in-demand skill and a domain up for grabs for the job-hungry and skilled personnel.
So the time is right to start learning Cyber Security today and become a part of this growing industry while it’s still in its initial stages. Try getting prepared with the Top 50 Cyber Security Questions and Answers to ace the entry to your dream job.
If the above stats have piqued your interest in making yourself a virtuous professional in Cyber Security, then start by enrolling at the right eLearning platforms.
I hope the above-mentioned Cyber Security project ideas help you to trail into the right academic path.
Get social